I came across this rant (with the usual don’t-kill-me-am-just-making-a-random-statement-and-fully-intend-to-get-away-with-it disclaimer) on LinkedIn about how CISO’s are clueless about how a virus works, even with CISA/CISM and a decade’s experience under their belt. It got me seething about how this statement is wrong on so many levels, but then I decided to marshal it in a better way and keyboard-and-mouse my thoughts (penning my thoughts would have sound a bit cliched, anyway) in a bit more structured way. I could be wrong but am willing to learn from feedback and remarks of my readers (if there are any. I am a realist).
A disclaimer first – I am not trying to promote anything here except my viewpoint.
CISO is 90% management, 10% technical post.
Let’s look at this line of thought.
Management, IMHO, is about making decisions without complete data at hand. This means that entire organization has to be put into an abstraction (nothing else will give a high level view that quickly). However, it results in a whole lot of jugglery and political skulduggery which has given a bad name to management. In an ideal world, every management guy has hands-on experience in everything that his company is doing. However, reality is different. Hence companies look for an ideal combination of practical know-how and management skills, with mixed results. Just like it is difficult for a management guy to learn technology, it is also difficult for a techie to learn management skills.
Companies seldom fail because of lack of technology. They fail due to lack of management / business sense and leadership (market disruptions notwithstanding) . It took a Steve Jobs to make Apple where it is now. It took Bill Gates’ decision making and management skills to make Microsoft where it is today.
Time for another disclaimer now.
I am not saying that Technology or techies are not needed. I am only saying that Management is also needed.
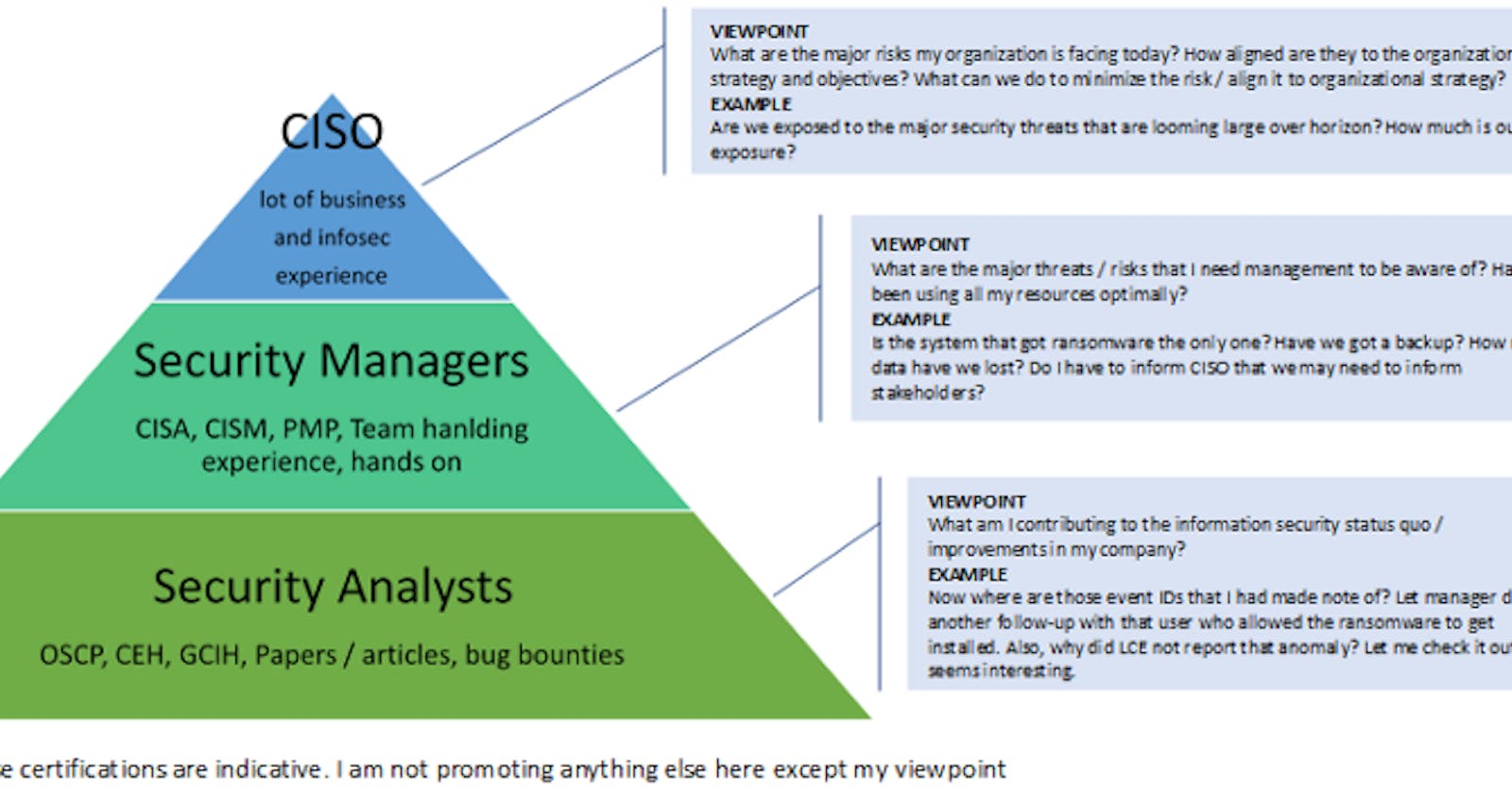
Time to look at an image that I created to illustrate my point. What I am trying to put here is the viewpoints of different roles in the information security food chain and an example of the viewpoint in action. See how abstraction builds up as roles get near to business.
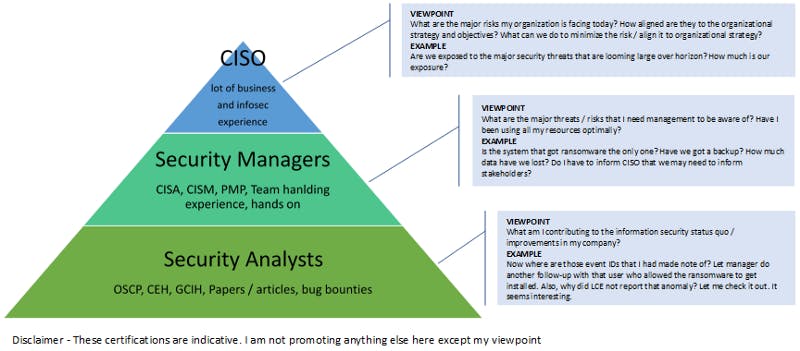
InfoSec FoodChain
As per Rafeeq Rehman (someone whom I admire a lot), below are the different activities that a CISO has to perform these days (http://rafeeqrehman.com/wp-content/uploads/2016/10/CISO_Job_v8_A0.pdf). You will notice that a lot of those activities are leadership activities and not technical. Although, technical knowledge is required, it is at an enabler level (in other words, understand what your team is saying so that you can make a decision), because CISO is essentially a decision maker / leader, sometimes a manager (if the company is small, CISO may also end up doing a bit of technical work himself). And, folks believe me when I say it – IT IS A FULL-TIME JOB.
Does a CISO need to know how a virus works? That is not the right question. The right question is –
Does a CISO need to know how a virus works in the same way as that of an incident responder under his team?
The answer is a resounding NO.
If you bring an OSCP (without the business experience) for CISO , you will suffer. And if you bring a CISA / CISM (without the necessary incident handling experience) for leading a team of incident handlers, my condolences.
CISA / CISM are technical certs, but not in the way you think.
Let me approach it in a different way.
I consider, anything that belongs to the know-how of the field, technical. So, detailed procedures on how to audit is technical stuff (related to audit). Its usage of software tools may be confined to MS Excel and Access, but it is still technical because it describes the innards of the field (e.g., how to sample, what is the meaning of audit, how is it different than assessment, how to do audit, etc.).
CISA (Certified Information System Auditors) is for auditors (present and wannabes) who audit information systems (security is a part of it). CISM (Certified Information Security Managers) is for managers (current and wannabes) who manage information security management systems. Together, they have a knowledge base that, if internalized, can help a person gain lot more insight into the field than without. That doesn’t mean everyone can stomach it. No so-called-techie can read CoBIT without falling asleep (that doesn’t mean that you claim yourself a techie just because you can’t stand CoBIT documentation), but a decision maker will immediately feel home with that documentation because it offers him a vantage point for the entire information security control landscape of an organization. Not just that, it will give him enough ammunition to oversee an existing information security system. Because the decision maker is used to see things in abstraction.
However, this also doesn’t mean that everyone who is a CISA / CISM has internalized all the knowledge that was part of the syllabus (you didn’t think I am vouching for incompetent guys, did you?). Which brings me to the next part.
Certifications are not knowledge pills, you still have to work your grey cells.
Having certifications only mean that you have cleared an exam. It doesn’t mean that you still retain, cross-reference, update, and internalize all that knowledge that was part of the syllabus, after the exam and in subsequent years. It also means that you still have to be interviewed for all those above verbs and your suitability to the role. I will stop here because this topic has been beaten so many times that it doesn’t make sense anymore to trample on the same. Just google “are information security certifications necessary” to know what I mean. Having a certification is no guarantee of job-material in this field.
Standards and Compliance are not bad things, neither are they cause of the current sad state of affairs. People are.
As far as I am concerned, all of our problems stem from increase in population. But that is for another post. Let’s focus on the current point.
Bruce Schneier made an interesting point in one of his books (I think it was “secrets and lies” but I am not sure) that firewalls got famous NOT because they were technically sound and made perfect sense, but because their absence was getting flagged as non-compliance by auditors! And you thought your CCIE made all the efforts!
With all the jokes running around compliance and ISO 27K1, I still think that the flaw is in the implementation, not in the spirit.
Security has so many facets these days that it is a full time job just to keep all the balls in air and make sure that they don’t crash. Add to it the daily pressure of selling security to top echelons so that you can keep your job lest a non-clued security director, or some other high title, decides that he doesn’t need you with all the flashy tools in place (SIEM / DLP / IDAM, once installed, must learn on its own) and you will sympathize with all the CISO’s since the term infosec was coined. Jokes apart, management needs someone who can translate the jargonic (wait, is that even a word?) aspects of security into a more manageable chunk so that they can decide where to direct the funding and oversight (in other words, tell me if it is working for business and show me how). Standards (like ISO 27001) and compliance / regulations are supposed to help a decision maker understand security in a language that they understand. But, as Ian Tibble points out so poignantly in his book “Security De-engineering”, excel masters took over and they took the whole focus away. And we have been cursing management ever since!
In other words (meaning I could have avoided all this rant and said these lines instead and still made my point): –
Security management and tech must co-exist to create a beautiful recipe that is tasteful to the business. Singular won’t work.